Dr. Yogesh Malhotra: LinkedIn:
Wall Street Investment Banks Quant : MIT AI-Machine Learning Industry Expert : Princeton Quant FinTech Presentations:
[AI, Algorithms & Machine Learning] [Quantitative Analytics] [Cybersecurity Risk Engineering] [Digital Transformation] [Quant Finance & Trading] [Cyber Finance]
Who's Who in America®, Who's Who in the World®,
Who's Who in Finance & Industry®, Who's Who in Science & Engineering®
MIT: AI & Machine Learning: Industry Expert: MIT AI-Machine Learning Executive Guide including RPA & Cognitive Automation.
Princeton University: Invited Presentations: AI, Machine Learning, Deep Learning: Princeton Quant FinTech Presentations.
Ranked among Finance & IT Nobel Laureates in AACSB and Scientific Impact Studies for Real World Impact of Research.
Download the PDF research reports titled:
Future of Bitcoin & Statistical Probabilistic Quantitative Methods:Global Financial Regulation (Interview: Hong Kong Institute of CPAs)
Bitcoin Protocol: Model of ‘Cryptographic Proof’ Based
Global Crypto-Currency & Electronic Payments System
| Bitcoin Protocol: Model of ‘Cryptographic Proof’ Based Global Crypto-Currency & Electronic Payments System |
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Yogesh Malhotra, PhD
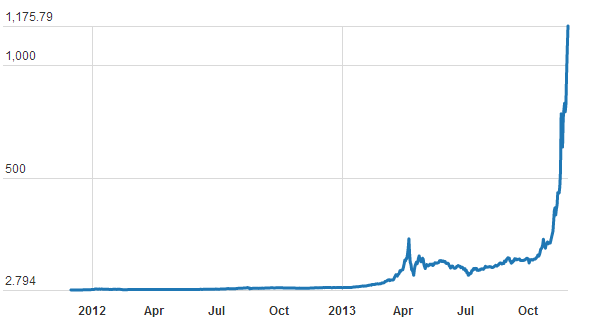
Future of Finance Project (www.FutureOfFinance.org), Global Risk Management Network, LLC, - Roubini launches stinging attack on bitcoin, CNBC, March 10, 2014. December 04, 2013 This research report represents the first known attempt with specific technical focus on cryptographic ‘proof of work’ in the context of virtual crypto-currencies such as Bitcoin. The cryptography, encryption and cryptanalysis technical focus of the report is intentional and related to Bitcoin’s innovative capabilities, vulnerabilities and threats. Money is an interesting construct that continues to occupy the fancy of many ranging from economists to quantum physicists... The future of money becomes "entangled" with future of money laundering when focus is not on privacy and anonymity alone, but also lack of traceability... Situated somewhere along the trajectory between real money and quantum money, virtual crypto-currencies based upon ‘cryptographic proof’ represent a natural stage in the evolution of global finance... The future of money, whatever form it may take – virtual or quantum, will quite likely be "entangled" with the future evolution of ‘cryptographic proof of work.’ The feasibility and large-scale global implementation of Bitcoin as a crypto-currency has earned it admiration as a remarkable conceptual and technical achievement and an elegant solution. Its cryptographic solution enables creation and regulation of issue of crypto-currency, preventing its counterfeiting and double-spending, and securing its global transmission at minimal transaction cost while using little time. Central to all those interesting innovations is the cryptographic ‘proof of work’ supplanting trust in a third-party that is the central focus of the current study. “The bitcoin protocol provides an elegant solution to the problem of creating a digital currency—i.e., how to regulate its issue, defeat counterfeiting and double-spending, and ensure that it can be conveyed safely—without relying on a single authority... It represents a remarkable conceptual and technical achievement, which may well be used by existing financial institutions (which could issue their own bitcoins) or even by governments themselves.” Bitcoin Protocol: Model of ‘Cryptographic Proof’ Based Abstract "For the importance of money essentially flows from its being a link between the present and the future." "You can know the name of a bird in all the languages of the world, but when you're finished, you'll know absolutely nothing whatever about the bird... So let's look at the bird and see what it's doing -- that's what counts." Introduction: Virtual Currency: Beginning of the End of Real Money? Virtual Currency and the Emergence of Bitcoin Crypto-Currency Bitcoins: Virtual Currency, Financial Instrument, or ‘Something Else’?
The pseudonymous Satoshi Nakamoto is characterized as the ‘inventor’ of Bitcoin. Various firms (Samsung, Toshiba, Nakamichi & Motorola as in SaToshi NakaMoto), and institutions such as the NSA (Nakamoto, SAtoshi) are identified among entities that may have ‘invented’ Bitcoin using the pseudonym. Some note similarity of pseudonym with Tatsuaki Okamoto, cited among references in the 1996 paper How to Make a Mint: The Cryptography of Anonymous Electronic Cash authored by National Security Agency’s Office of Information Security Research and Technology Cryptology Division. Twelve years before the Bitcoin paper, the NSA paper, based upon its review of electronic cash schemes, made notable observations. It noted that cryptography underlying those schemes seemed fine and delivered promised anonymity. It also observed however that those schemes seemed not as satisfactory from a law enforcement point of view: “In particular, the dangers of money laundering and counterfeiting are potentially far more serious than with paper cash. These problems exist in any electronic payment system, but they are made much worse by the presence of anonymity. Indeed, the widespread use of electronic cash would increase the vulnerability of the national financial system to Information Warfare attacks.” Bitcoin: A ‘Cryptographic Proof’ Based P2P Electronic Payment System Bitcoin Addresses & Public Key Cryptography Bitcoin Transactions & Digital Signatures Based on ECDSA
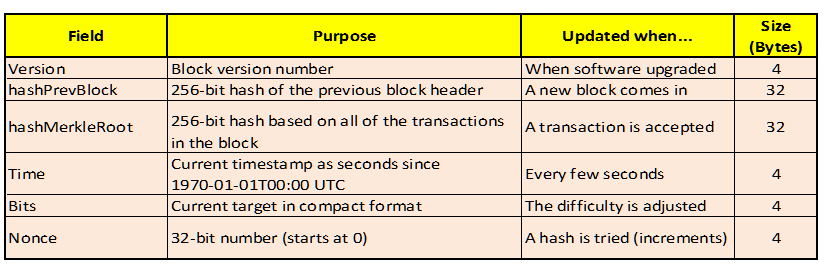
A public key can be computed from a private key, but it is presumably computationally infeasible to do vice-versa. A public key can be used to authenticate or confirm the validity of the digital signature. As shown in Figure 2 above, address N transfers the payment to address M by digitally signing using its private key the mathematically generated hash H of prior transaction TN and public key of address M. Also, as shown, the digital signature of address N can be verified by using N’s public key without knowing its private key. The Bitcoin block chain contains all such transactions ever executed wherein each block contains the SHA-256 hash of the previous block.
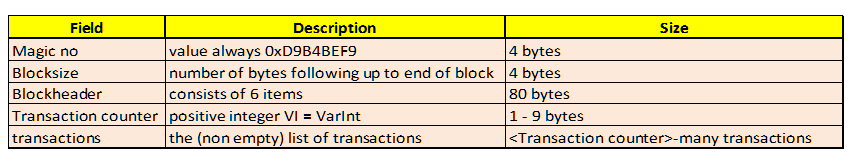
Bitcoin address is computed directly from the HASH160 value as illustrated below in Figure 3, where base58 is a binary-to-text encoding scheme: Organizing Transactions into Blocks and Time Stamping Them
|
  |
  |
  |
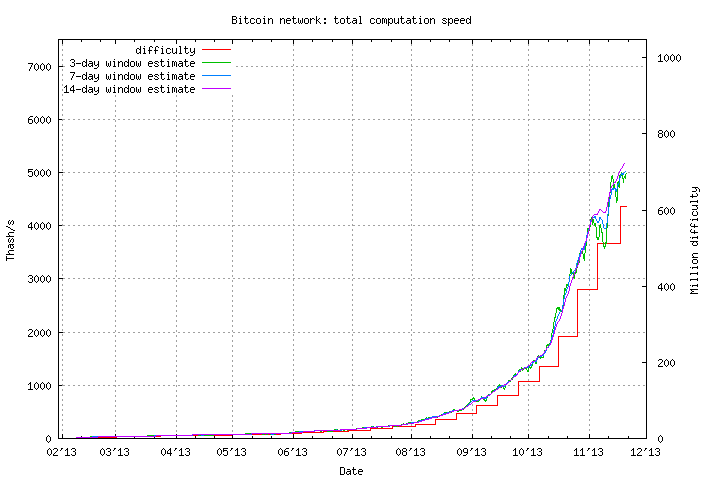
With many online websites and services dedicated to tracking BTC markets and transactions, a quick snapshot of the ‘BTC Economy’ from one such site bitcoinwatch.com is shown in Figure 11. Some interesting numbers from those statistics include: current total 12,061,150 BTCs with market cap 12,248,339,048 USD, 8.29 blocks generated per hour, and network hashrate of 66840.80 PetaFLOPS. Also, it is clear that BTCChina is the predominant BTC exchange leader after overtaking lead from Mt. Gox.

Figure11. The 'Bitcoin Economy' Overview Snapshot
Cryptographic Proof as Substitute for Trust in Third Party
When a miner finds a suitable block hash, he couples it with a nonce and broadcasts it to the network. Resulting hash is combined with previous completed block hash along with the BTCs being exchanged thus forming the block chain. The block chain represents the ‘trust’ of each transaction because each new transaction block is generated based on the unique hash of the previous block of all prior transactions. The entire history of every transaction can be traced back through the longest chain that is ‘trusted’ by all P2P nodes which keep extending it further. Because the network trusts the longest continuous block chain and a suitable SHA-256 hash may take 10 minutes or so to generate, an attack would require more computational power than all honest nodes combined. To pre-empt such possibility, a block is not considered final until it is 6 links deep which may take up to an hour. The distributed timestamp server generates proof of chronological order of transactions and the system is supposed to be secure unless a group of attacker nodes can collectively control more CPU power than honest nodes.
Known and Potential Attacks and Vulnerabilities of Bitcoin
Pros and cons of Bitcoin as well as potential weaknesses in its security and encryption protocols were discussed above; other potential vulnerabilities are summarized below. Most probably, the pseudonymous Bitcoin inventor didn’t envision today’s global BTC mining computational arms-race with armies of botnets using global captive computers, software vendors using malware to steal customers’ CPU power for mining BTCs, or clearly illegal service using ransom-ware forcing law enforcement officers into making BTC payments via their openly public customer service Web site.
Bitcoin is known for its [pseudo-]anonymity of user identification as it uses randomly generated public keys for Bitcoin addresses; however, it is not truly anonymous. As noted in the US Senate Hearing testimony of the Criminal Division: “Criminals are drawn to services that allow users to conduct financial transactions while remaining largely anonymous… [However,] To be clear, virtual currency is not necessarily synonymous with anonymity.” Public key addresses are self-identified by users for receiving payments or when they need to convert BTCs to other currencies including real money when user identity is linked with related public key address. Furthermore, different public keys that are input in a specific transaction or a sequence of transactions can be related to the specific users and the private keys used for sending payments need to be known to the transmitting exchanges. Also, change addresses used for returning residual ‘change’ from Bitcoin transactions can be linked to respective input addresses as well as input users. Private transactions between parties of same exchange are privy to the exchange which may be able to bypass such identification by not using the strict Bitcoin protocol of transparency of each transaction. The ‘default’ Bitcoin protocol doesn’t provide true anonymity which may require protection from both forward attacks and reverse attacks. Forward attacks involve getting something that identifies a user using coins received with methods that should remain secret. Reverse attacks involve getting something that should remain secret by using coins that can identify a user.
Several additional ‘weaknesses’ representing vulnerability of Bitcoin coins and transactions are identified next. Wallet files are vulnerable to theft and need to be encrypted and backed off-line. Old backup wallet files and contents can be retrieved with existing backup facilities. Coin’s history can be traced to link user identities to the pseudo-anonymous addresses. Unlike Bitcoin addresses, if a payment is sent to IP address, man-in-the-middle attack is feasible given IP addresses can be spoofed. Unless node-to-node encryption is used, packet sniffing can reveal the sent transactions. Distributed denial of service (DDoS) attacks pose potential threats just like with any other networked cryptographic service. However, deep-pocketed DDoS attacks using ‘remarkable 100 G/bits per second in bandwidth’ and million-dollar hacking heists are becoming increasingly common. Timejacking attacks can be done by announcing inaccurate timestamps when connecting to a node where an attacker can deceive it into accepting an alternate block chain by altering the node's network time counter. Results may range between increased chances of double-spending, drained computational resources, and slower transaction rates. Potential causes for concern for miners also include: more efficient mining gear only raises the network ‘difficulty’ without reducing energy use and cheaper energy linearly increases mining energy use. Similar concerns apply to other cryptographic proof of work currencies such as Litecoin as well.
Besides vulnerabilities of encryption protocols to available quantum computers, classical computers capable of 54.9-petaflops may pose major ‘>50%’ threat to Bitcoin. The specific attack results from anyone in the network acquiring more than 50% computing power being able to exclude, modify, and self-reverse transactions and prevent some or all ‘mining’ of valid blocks. Even with less than 50% power such attacks are feasible: e.g. someone with 40% of network computing power can overcome a 6-deep confirmed transaction with a 50% success rate. Nevertheless, it is exponentially difficult to change historical blocks going back in time and it isn’t possible to change blocks created before the last checkpoint. Even though a profit-seeking attacker potentially may gain from following the protocol or launching other attacks, however, “if the above attack is successfully executed, it will be difficult or impossible to "untangle" the mess created -- any changes the attacker makes might become permanent.” Given individual mining pools have controlled 25% to 33% of mining power, a Cornell study, argues that >50% attack is feasible even though developers seem not as concerned.
Double spending attacks to which the Bitcoin protocol is vulnerable include Race attack, Finney attack, Vector76 attack, Brute force attack, and >50% attack. The research study Two Bitcoins at the Price of One found that the Bitcoin protocol is highly susceptible to Race attacks. Such attacks involve successfully sending one transaction to a merchant while sending different transaction spending same coins that were first sent to eventually make it into the block chain. The Finney attack is another fraudulent attack requiring the miner’s participation once a block has been mined with a conflicting transaction not yet announced to the network. While a miner verifying the block that contains money sent by someone to oneself, the sender may find the block and send the money to someone else. The sender receives his money while the legitimate transaction is rejected as the same money can’t be double spent. Vector76 attack is a combination of the above two attacks such that a transaction that even has one confirmation can still be double-spent. In a Brute force attack, the attacker submits to the merchant or network a transaction which pays the merchant, while privately mining a blockchain fork in which a double-spending transaction is included instead. In >50% attack discussed earlier, the attacker simply perseveres with private fork generating blocks faster than the rest of the network until he controls the longest branch superseding those of the honest network.
Future of Bitcoin and Other Crypto-Currencies
In his letter of September 06, 2013, the Chairman of the US Federal Reserve, quoting a 1995 US House of Representatives hearing, noted that: “while [virtual currency] innovations may pose risks related to law enforcement and supervisory matters, there are also areas in which they may hold long-term promise, particularly if the innovations promote a faster, more secure and more efficient payment system.” In many ways, despite their notorious widespread use in illegal activities the current popular appeal of crypto-currencies such as Bitcoin seems to stem from the innovations that the Fed Chairman and the Chicago Fed mentioned in their respective documents. In his letter, the Fed Chairman underscored the need for regulatory compliance on part of public and private players in electronic cash and related banking and finance industries. On the other hand, there is the search for true anonymity and privacy on part of some academics and practitioners besides users of such crypto-currencies as discussed. The future of cryptography, cryptanalysis, and crypto-currencies is anticipated to evolve based upon reconciliation of expectations, needs, and wants of diverse stakeholders.
A snapshot of the current contenders for that future of crypto-currencies is displayed in this concluding discussion. Currently, there are 30 to 40 virtual currencies listed. Figure 12 lists a comparison of top-30 showing 20-fold lead of Bitcoin over Litecoin.
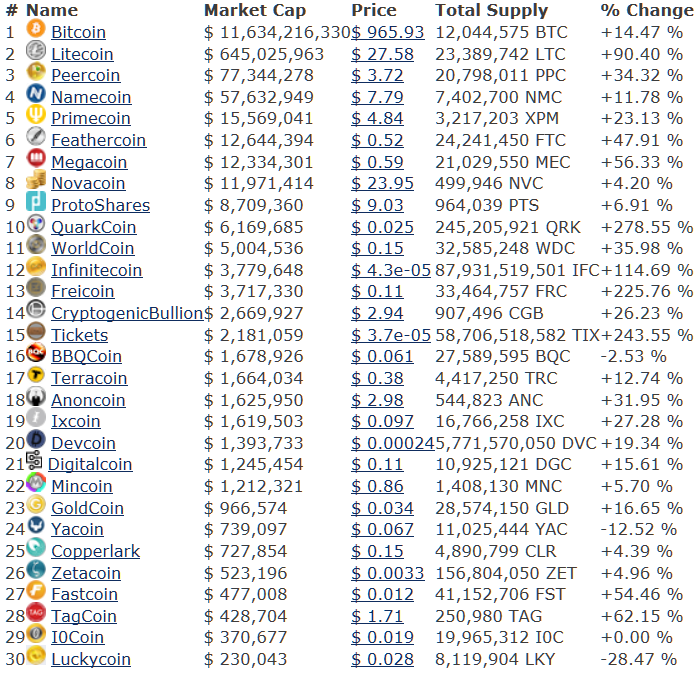
Figure12. How the Current Crop of Virtual Currencies Stack Up
Such virtual currencies are also known as alt-coins for alternative crypto-currencies. alt-coins based upon SHA-256, the hashing algorithm for Bitcoin, include NMC: Namecoin, PPC: PPCoin (Peercoin), DVC: Devcoin, TRC: Terracoin, BTE: Bytecoin, IXC: Ixcoin, I0C: I0coin, FRC: Freicoin, and BLC: Blakecoin. In contrast, alt-coins such as Litecoin using scrypt, a password-based key derivation function that cannot be mined using ASICs, include besides LTC: Litecoin, NVC: Novacoin, FTC: FeatherCoin, MNC: MinCoin, BBQ: BBQcoin, TAG: Tagcoin, MEG: Memorycoin, and BTCs/BTC2: Bitcoin Scrypt. Like Bitcoins, most of these virtual currencies are mined similarly by using cryptographic proof of work concepts. Given central role in making the crypto-currencies possible, ‘cryptographic proof of work’ is anticipated to have a longer shelf-life than any of the above currencies. The future of money, whatever form it may take – virtual or quantum, will quite likely be "entangled" with the future evolution of ‘cryptographic proof of work.’ Hence, the focus of this report has been on most central concept underlying the current trajectory of e-evolution of money and global payments.
Conclusion
This research report represents the first known attempt with specific technical focus on cryptographic ‘proof of work’ in the context of virtual crypto-currencies such as Bitcoin. The cryptography, encryption and cryptanalysis technical focus of the report is intentional and related to Bitcoin’s innovative capabilities, vulnerabilities and threats. Situated somewhere along the trajectory between real money and quantum money, virtual crypto-currencies based upon ‘cryptographic proof’ represent a natural stage in the evolution of global finance. The feasibility and large-scale global implementation of Bitcoin as a crypto-currency has earned it admiration as a remarkable conceptual and technical achievement and an elegant solution. Its cryptographic solution enables creation and regulation of issue of crypto-currency, preventing its counterfeiting and double-spending, and securing its global transmission at minimal transaction cost while using little time. Central to all those interesting innovations is the cryptographic ‘proof of work’ supplanting trust in a third-party that is the central focus of the current study.
Bibliography:
- Ben S. Bernanke. Letter to the U.S. Senate Committee on Homeland Security & Governmental Affairs. Board of Governors of the Federal Reserve System. September 6, 2013.
- Joppe W. Bos, J. Alex Halderman, Nadia Heninger, Jonathan Moore, Michael Naehrig, and Eric Wustrow. Elliptic Curve Cryptography in Practice. Microsoft Research. November 2013.
- H. Dobbertin, A. Bosselaers, and B. Preneel, 'RIPEMD-160, A Strengthened Version of RIPEMD, Fast Software Encryption, LNCS 1039, D. Gollmann, Ed., Springer-Verlag, 1996, pp. 71-82.
- Economist. Technology Quarterly. Bitcoin under pressure. Q4 2013. Nov 30th 2013.
- Ittay Eyal and Emin Gun Sirer. Majority is not Enough: Bitcoin Mining is Vulnerable. Computer Science > Cryptography and Security, Cornell University Library. November 15, 2013.
- Federal Financial Institutions Examination Council. Bank Secrecy Act / Anti-Money Laundering Examination Manual. 2010.
- Timothy A Hall. The FIPS 186-3 Digital Signature Algorithm Validation System (DSA2VS). National Institute of Standards and Technology. Updated: September 5, 2013.
- Danny Yuxing Huang, Hitesh Dharmdasani, Sarah Meiklejohn, Kirill Levchenko, Alex C. Snoeren, Stefan Savage, Nicholas Weaver, Chris Grier, and Damon McCoy. Poster: Botcoin - Bitcoin-Mining by Botnets. IEEE Security. Spring 2013.
- Nicola Jones. Google and NASA Snap Up Quantum Computer D-Wave Two. Scientific American. May 17, 2013.
- Ghassan O. Karame, Elli Androulaki and Srdjan Capkun. Two Bitcoins at the Price of One? Double-Spending Attacks on Fast Payments in Bitcoin. IACR Cryptology ePrint Archive. 2012.
- Laurie Law, Susan Sabett, and Jerry Solinas. How To Make A Mint: The Cryptography Of Anonymous Electronic Cash. National Security Agency Office of Information Security Research and Technology, Cryptology Division. National Security Agency. 18 June 1996.
- Yogesh Malhotra. Quantum Computing, Quantum Cryptography, Shannon's Entropy and Next Generation Encryption & Decryption. Global Risk Management Network, LLC, 2013.
- Yogesh Malhotra. Cryptology Beyond Shannon's Information Theory: Preparing for When the 'Enemy Knows the System'. Global Risk Management Network, LLC, 2013.
- Yogesh Malhotra. Number Field Sieve Cryptanalysis Algorithms for Most Efficient Prime Factorization on Composites. Global Risk Management Network, LLC, 2013.
- Sarah Meiklejohn, Marjori Pomarole, Grant Jordan, Kirill Levchenko, Damon McCoy, Geoffrey M. Voelker, and Stefan Savage. A Fistful of Bitcoins: Characterizing Payments Among Men with No Names, Proceedings of the ACM Internet Measurement Conference, Barcelona, Spain, October 2013.
- Florian Mendel, Tomislav Nad, Stefan Scherz, and Martin Schläffer. Differential Attacks on Reduced RIPEMD-160, Lecture Notes in Computer Science Volume 7483, 2012, pp. 23-39.
- Florian Mendel, Thomas Peyrin, Martin Schläffer, Lei Wang, and Shuang Wu. Improved Cryptanalysis of Reduced RIPEMD-160, Lecture Notes in Computer Science Volume 8270, 2013, pp 484-503.
- Satoshi Nakamoto. Bitcoin: A Peer-to-Peer Electronic Cash System. November, 2008.
- Peter W. Shor, Edward Farhi, David Gosset, Avinatan Hassidim, and Andrew Lutomirski. Quantum Money. MIT. January 19, 2012.
- Michael A. Nielsen and Isaac L. Chuang. Quantum Computation and Quantum Information: 10th Anniversary Edition. Cambridge University Press. January 31, 2011.
- NIST. FIPS Pub 180-4: Federal Information Processing Standards Publication Secure Hash Standard (SHS). Information Technology Laboratory, National Institute of Standards and Technology. March 2012.
- NIST. NIST Special Publication 800-90A: Recommendation for Random Number Generation Using Deterministic Random Bit Generators. January 2012.
- NIST. Supplemental ITL Bulletin For September 2013: NIST Opens Draft Special Publication 800-90A, Recommendation For Random Number Generation Using Deterministic Random Bit Generators, For Review And Comment. September 2013.
- B. Preneel, A. Bosselaers, and H. Dobbertin. The cryptographic hash function RIPEMD-160. CryptoBytes, Vol. 3, No. 2, 1997, pp. 9-14.
- Somitra K. Sanadhya and Palash Sarkar. Non-linear Reduced Round Attacks against SHA-2 Hash Family. ACISP '08 Proceedings of the 13th Australasian conference on Information Security and Privacy, 2008, pp. 254 - 266.
- Yu Sasaki, Lei Wang, and Kazumaro Aoki. Preimage Attacks on 41-Step SHA-256 and 46-Step SHA-512. IACR Cryptology ePrint Archive. 2009.
- William Stallings. Inside SHA-3. IEEE Potentials, November/December 2013, pp. 26-31.
- U.S. Senate Committee on Homeland Security & Governmental Affairs. Beyond Silk Road: Potential Risks, Threats, and Promises of Virtual Currencies. November 18, 2013.
Footnotes:
- http://spectrum.ieee.org/static/future-of-money
- http://quantum.nasa.gov/materials/2012-01-19-B1-Shor.pdf
- http://spectrum.ieee.org/at-work/innovation/the-beginning-of-the-end-of-cash
- http://spectrum.ieee.org/computing/networks/whos-who-in-bitcoin-zerocoin-hero-matthew-green
- http://spectrum.ieee.org/computing/software/bitcoin-the-cryptoanarchists-answer-to-cash
- http://www.hsgac.senate.gov/download/?id=705a1d48-e7fc-4706-b192-13790789c559
- http://www.hsgac.senate.gov/hearings/beyond-silk-road-potential-risks-threats-and-promises-of-virtual-currencies
- http://www.hsgac.senate.gov/download/?id=705a1d48-e7fc-4706-b192-13790789c559
- http://techcrunch.com/2013/08/19/germany-recognizes-bitcoin-as-private-money-sales-tax-coming-soon/
- http://www.ft.com/intl/cms/s/0/9ecefa7c-bda6-11e2-890a-00144feab7de.html
- http://www.ffiec.gov/bsa_aml_infobase/documents/bsa_aml_man_2010.pdf
- http://online.wsj.com/public/resources/documents/VCurrenty111813.pdf
- http://www.cnbc.com/id/101233864
- http://www.forbes.com/sites/gordonchang/2013/11/24/a-china-triangle-bitcoin-baidu-and-beijing/
- http://www.forbes.com/sites/gordonchang/2013/11/24/a-china-triangle-bitcoin-baidu-and-beijing/
- http://www.cnbc.com/id/101225781
- http://www.cnbc.com/id/101230884
- http://Bitcoinexaminer.org/who-is-satoshi-nakamoto/, http://Bitcointalk.org/index.php?topic=235342.0.
- http://groups.csail.mit.edu/mac/classes/6.805/articles/money/nsamint/nsamint.htm
- http://groups.csail.mit.edu/mac/classes/6.805/articles/money/nsamint/nsamint.htm
- http://www.newyorker.com/reporting/2011/10/10/111010fa_fact_davis
- http://sc5.io/blog/2013/02/sc5er-intro-the-bitcoin-guy/
- http://www.marketwatch.com/story/bitcoin-swing-widens-drops-to-over-500-from-900-2013-11-19
- http://www.theverge.com/2013/5/6/4295028/report-satoshi-nakamoto
- http://www.reuters.com/article/2013/11/18/us-senate-virtualcurrency-idUSBRE9AH0P120131118
- http://www.forbes.com/sites/andygreenberg/2013/11/18/meet-the-assassination-market-creator-whos-crowdfunding-murder-with-bitcoins/
- http://spectrum.ieee.org/computing/software/bitcoin-the-cryptoanarchists-answer-to-cash
- http://spectrum.ieee.org/computing/networks/whos-who-in-bitcoin-zerocoin-hero-matthew-green
- http://spectrum.ieee.org/computing/software/bitcoin-the-cryptoanarchists-answer-to-cash
- http://csrc.nist.gov/groups/STM/cavp/documents/dss2/dsa2vs.pdf
- http://research.microsoft.com/apps/pubs/default.aspx?id=204914
- http://homes.esat.kuleuven.be/~bosselae/ripemd160.html
- http://en.bitcoin.it/wiki/Base58Check_encoding
- http://www.wired.com/threatlevel/2013/09/rsa-advisory-nsa-algorithm/
- http://csrc.nist.gov/publications/nistbul/itlbul2013_09_supplemental.pdf
- http://csrc.nist.gov/publications/nistpubs/800-90A/SP800-90A.pdf
- http://en.bitcoin.it/wiki/Block
- http://en.bitcoin.it/wiki/Genesis_block
- http://en.bitcoin.it/wiki/Nonce
- http://csrc.nist.gov/publications/nistpubs/800-90A/SP800-90A.pdf
- http://csrc.nist.gov/publications/fips/fips180-4/fips-180-4.pdf
- http://eprint.iacr.org/2009/479.pdf
- http://eprint.iacr.org/2008/174.pdf
- http://eprint.iacr.org/2011/037.pdf
- http://www.cosic.esat.kuleuven.be/publications/article-317.pdf
- http://online.tugraz.at/tug_online/voe_main2.getvolltext?pCurrPk=65186
- http://eprint.iacr.org/2013/600.pdf
- http://app.box.com/shared/static/zv3wj7bnaeel3odfd4r3.pdf
- http://www.computerworld.com/s/article/9239710/China_surpassing_U.S._with_54.9_petaflop_supercomputer
- http://www.cambridge.org/us/academic/subjects/physics/quantum-physics-quantum-information-and-quantum-computation/quantum-computation-and-quantum-information
- http://www.wired.com/wiredenterprise/2013/11/quantum_nasa/
- http://www.scientificamerican.com/article.cfm?id=google-nasa-snap-up-quantum-computer-dwave-two
- http://www.wired.com/wiredenterprise/2013/06/d-wave-quantum-computer-usc/
- http://bitcoin.org/bitcoin.pdf
- http://www.yogeshmalhotra.com/MalhotraYogesh_CryptanalysisReport.pdf
- http://en.bitcoin.it/wiki/Mining_hardware_comparison
- http://krebsonsecurity.com/2013/07/botcoin-bitcoin-mining-by-botnet/
- http://www.bitcoinx.com/profit/
- http://en.bitcoin.it/wiki/Difficulty
- http://en.bitcoin.it/wiki/Blocks
- CPU: central processing unit, GPU: graphics processing unit, FPGA: field-programmable gate array, ASIC: application-specific integrated circuit
- http://www.economist.com/news/technology-quarterly/21590766-virtual-currency-it-mathematically-elegant-increasingly-popular-and-highly
- http://www.economist.com/news/technology-quarterly/21590766-virtual-currency-it-mathematically-elegant-increasingly-popular-and-highly
- http://www.ieee-security.org/TC/SP2013/posters/Danny_Yuxing_Huang.pdf
- http://krebsonsecurity.com/2013/07/botcoin-bitcoin-mining-by-botnet/
- http://www.wired.com/wiredenterprise/2013/11/e-sports/
- http://news.techworld.com/security/3489937/us-police-department-pays-750-cryptolocker-trojan-ransom-demand/
- http://www.justice.gov/opa/pr/2013/November/13-crm-1230.html
- http://cseweb.ucsd.edu/~smeiklejohn/files/imc13.pdf
- http://en.bitcoin.it/wiki/Anonymity
- http://en.bitcoin.it/wiki/Anonymity
- http://en.bitcoin.it/wiki/Weaknesses
- http://www.networkworld.com/news/2013/060713-bitcoin-facts-270605.html
- http://www.wired.com/wiredenterprise/2013/11/ddos_bitcoin/
- http://www.wired.co.uk/news/archive/2013-11/29/bitcoin-hack-heists
- http://culubas.blogspot.com/2011/05/timejacking-bitcoin_802.html
- http://www.wired.com/wiredenterprise/2013/11/quantum_nasa/
- http://www.scientificamerican.com/article.cfm?id=google-nasa-snap-up-quantum-computer-dwave-two
- http://www.wired.com/wiredenterprise/2013/06/d-wave-quantum-computer-usc/
- http://www.computerworld.com/s/article/9239710/China_surpassing_U.S._with_54.9_petaflop_supercomputer
- http://en.bitcoin.it/wiki/Double-spending
- http://en.bitcoin.it/wiki/Weaknesses
- http://hackingdistributed.com/2013/11/04/bitcoin-is-broken/
- http://arxiv.org/abs/1311.0243
- http://www.forbes.com/sites/kashmirhill/2013/11/06/bitcoin-is-not-broken/
- http://en.bitcoin.it/wiki/Double-spending
- http://eprint.iacr.org/2012/248.pdf
- http://online.wsj.com/public/resources/documents/VCurrenty111813.pdf
- http://en.wikipedia.org/wiki/List_of_cryptocurrencies
- http://www.forbes.com/sites/reuvencohen/2013/11/27/the-top-30-crypto-currency-market-capitalizations-in-one-place/
- http://en.wikipedia.org/wiki/Scrypt
- http://altcoins.com/
| "There are many definitions of knowledge management. It has been described as "a systematic process for capturing and communicating knowledge people can use." Others have said it is "understanding what your knowledge assets are and how to profit from them." Or the flip side of that: "to obsolete what you know before others obsolete it." (Malhotra) " - U.S. Department of Defense, Office of the Under Secretary of Defense (Comptroller) |
 |
| "KM is obsoleting what you know before others obsolete it and profit by creating the challenges and opportunities others haven't even thought about -- Dr. Yogesh Malhotra, Inc. Technology" - U.S. Defense Information Systems Agency Interoperability Directorate |
 |
| "If you spend some time at [the digital research lab] founded by Dr. Malhotra you will be blessed by some of the world's most astute thinking on the nature of knowledge and its value." - U.S. Army Knowledge Symposium, Theme: "Knowledge Dominance: Transforming the Army...from Tooth to Tail", Department of Defense, United States Army. |
 |
| "We are observing diminishing credibility of information technologists. A key reason for this is an urgent need to understand how technologies, people and processes together combine to influence enterprise performance. Today's effective CIO doesn't deliver IT. He delivers business transformation services." - Yogesh Malhotra, Journal of Knowledge Management, 2005 - United States Air Force Research Lab CIO Col. Tom Hamilton in presentation to the Armed Forces Communications Electronics Association titled 'Enterprise IT Solutions Are Tough But They're Tougher If You're Stupid', July 21, 2005. |
 |
| "Knowledge Management refers to the critical issues of organizational adaptation, survival and competence against discontinuous environmental change. Essentially it embodies organizational processes that seek synergistic combination of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings." -- Yogesh Malhotra - United States Department of Navy |
 |
| "Dr. Yogesh Malhotra, PhD, drawing upon numerous sources, proposes several theories as to how IT can be used to drive the change of organizations. As environments become more turbulent, organizations must adapt at the same rate to maintain its advantage. Among his theories are that the turbulent environments (in this case, business, but can translate to the turbulent military conflict environment) drive organizations to use IT for empowering workers at all levels, increasing span of control, and increasing lateral communications." - United States Marine Corps, Reorganization Of The Marine Air Command And Control System To Meet 21St Century Doctrine And Technology, Thesis, September 2001. |
 |
| "The self-organizing capacity of dynamically adaptive systems is amazing. They tend to eliminate redundancy, minimize connections, and establish priorities--all without outside direction. When something is organized, we tend to believe that someone organized it, some outside influence. But that's not necessarily so. Self-organization is a process in which the organization of a system occurs spontaneously based on the action of its members, without this process being controlled by an external system. The richness of possible behavior increases rapidly with the number of interconnections and the level of feedback. (Malhotra) " - U.S. Army War College Quarterly |
 |
| "Dr. Malhotra argues in Business Process Redesign that reengineering is the notion of discontinuous thinking -- recognizing and breaking away from outdated rules and fundamental assumptions. He suggests that reengineering principles are organized around outcomes, and that people who use the output should perform the process. This links parallel activities instead of integrating results, and puts the decision point where the work is performed (Malhotra, 1996). Integrating the DPW processes further into the installation staff can achieve these outcomes. Seventy percent of Business Process Redesigns (BPR) fail because of business focus on cost-cutting and narrow technical approaches (Malhotra, 1996). The installation commanders should decide how DPWs could best serve the community. They should have the opportunity to focus on efficient output and not on restructuring to cut cost. Developing the Corps as the primary service provider narrows the commander's options and does not solve the problem, merely the symptoms. The ultimate success of BPR depends on the experience of people who execute it and how well they apply their creativity to redesigning the processes." - U.S. Army Management Staff College |
 |
| "These activities are often described as "knowledge management." See Knowledge Management, in the World Wide Web Virtual Library, edited by Yogesh Malhotra. (Accessed June 16, 1998)....The terms "marshalling" and "mobilization" are intended here to represent two major activities of knowledge management in U.S. national security decisionmaking. Although others may describe and classify basic knowledge-building activities differently, "knowledge management" has been accepted as an umbrella term. See. for example, TheWorld Wide Web Virtual Library on Knowledge Management, edited by Yogesh Malhotra, (Accessed June 16, 1998)..." - U.S. Air Force Colonel Roc A. Myers, Colonel (s), Harvard University Air Force National Defense Fellow with the Program in 1997-98. Strategic Knowledgecraft: Operational Art for the Twenty-First Century, Roc A. Myers, Prepared while an Air Force National Defense Fellow with the Program in 1997-98 (September 2000). |
 |
| "Seventy percent of BPR projects fail. Three primary obstacles inhibit the success of reengineering projects: Lack of sustained management commitment and leadership -- It is critical that senior leadership not only support BPR but also be a vocal advocate. Unrealistic scope and expectations -- It is important to manage expectations. BPR is not a panacea that will cure all ills. Resistance to change -- The world is changing all the time and the pace of change continues to accelerate. It will continue to change whether we participate or not. We must change with it or be left behind. AIT provides AIS program managers the opportunity to completely reexamine and reengineer their entire business process, because it offers capabilities not previously available in terms of timeliness and accuracy of data capture. During the operational prototype, the Air Force provided an excellent example of a reengineered business process as a result of AIT. The Supply Asset Tracking System (SATS) is a front-end server that integrates AIT with the supply AIS, the Standard Base Supply System (SBSS). SATS uses linear bar codes for tracking and inventory purposes and smart cards for personal identification to verify receipt and establish personal accountability of property. (Malhotra) " - U.S. Department of Defense Logistics Implementation Plan |
 |
| "Knowledge Management caters to the critical issues of organisational adaption, survival and competence in the face of increasingly discontinuous environmental change ... Essentially, it embodies organisational process that seek synergistic combination of data and information processing capacity of information technologies and the creative and innovative capacity of human beings." - Yogesh Malhotra - Royal Australian Air Force (RAAF) AIRCDRE John Blackburn, Director General Policy and Planning - Air Force (DGPP-AF), Royal Australian Air Force (RAAF), in Air Power Conference 2000. |
 |
| "First intangible assets are defined in relation to core competencies of the firm. Each core competence is a combination of intangible assets such as knowledge and skills, standards and values, explicit know-how and technology, management processes and assets, and endowments such as image, relationships, and networks. Knowledge creation is the core competence of any firm (Malhotra, 2000)." - Government of UK, Ministry of Defence |
 |
| "Malhotra noted the importance of Information Systems for organizational learning, mentioning a series of techniques, methods and tools that can foster organizational learning at many steps of the process: knowledge acquisition, creation and distribution [Malhotra, 1996]." - Canadian Department of National Defence, Canada, Defence R&D Canada |
 |
| "Knowledge Management caters to the critical issues of organisational adaption, survival and competence in the face of increasingly discontinuous environmental change. Essentially, it embodies organisational process that seek synergistic combination of data and information processing capacity of information technologies and the creative and innovative capacity of human beings. -- Yogesh Malhotra" - Air Force, Australia, Director General Policy and Planning |
 |
| "According to Malhotra, KM ensures that right knowledge is applied at the right place and time and it is about doing the right thing instead of doing things right. Its application to R&D will avoid unnecessary duplication of research. It can help support both individual and organizational learning from past successes and failures while guiding future actions and changes." - International Atomic Energy Agency |
 |
| "The Knowledge Management (KM) area has become so diverse over the past ten years as researchers have begun to investigate not only the mechanics of knowledge creation and transfer but also of social and cultural issues that are of importance in understanding this topic. KM is the process of leveraging and utilizing the vast, untapped potential of both implied and documented knowledge to achieve optimal performance, both are equally important for improving performance. Knowledge Management enables businesses to exchange and optimize the knowledge and experience. "Knowledge Management caters for the critical issues of organisational adoption, survival and competence in face of increasingly discontinuous environmental change. Essentially, it embodies organizational processes that seek synergistic combination of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings" (Dr. Yogesh Malhotra 1997)." - IBM |
 |
| "In his latest book, Knowledge Management and Virtual Organisations, KM luminary, Dr. Yogesh Malhotra, offers some cautionary advice. He exposes three myths often associated with KM solutions. The first of these is that knowledge management technologies can deliver the right information to the right person at the right time. This assumes businesses will develop incrementally in stable markets. However as Malhotra says, "the new business model in the Information Age is marked by fundamental, not incremental change. Businesses can't plan long-term; instead, they must shift to a more flexible 'anticipation of surprise' model. Thus it is impossible to build a system that predicts who the right person at the right time even is, let alone what constitutes the right information." - Microsoft Corporation |
 |
| "All can be used to further the goal of keeping the channels of communication open to allow for the exchange of issues and ideas within an organization. According to BRINT Institute chairman and CKO Dr. Yogesh Malhotra, "The key issue is not about the latest information technologies, but whether those technologies are used within, and for facilitating, a culture of information sharing, relationship building and trust." With communication and trust, set within the solid framework of a component architecture, your business can harness that elusive ability to get the right information to the right people at the right time for the right business purposes." - Cisco Systems, Inc. |
 |
| "According to Yogesh Malhotra, Knowledge Management practitioner and web author, "Knowledge Management is a brand new field emerging at the confluence of organization theory, management strategy, and management information systems." Breaking apart this definition, Knowledge Management can be defined as an internal, corporate strategy. Knowledge Management can also stand alone as a separate, Information Technology program. Malhotra is right on target when he states that Knowledge Management is a brand new field. Knowledge Management began receiving airplay in 1996. At that time, Tom Davenport wrote in CIO Magazine that a chief knowledge officer "captures and leverages structured knowledge, with information technology as a key enabler." Expanding upon Malhotra and Davenport's definitions, Knowledge Management within NCR Corporation can be defined via a business objective (strategic), a method of Knowledge Management delivery (the management information system), and a role within the organization. NCR's objective is to create, capture, and disseminate knowledge." - NCR Corporation |
 |
| "Institutionalization of 'best practices' by embedding them in information technology might facilitate efficient handling of routine, 'linear,' and predictable situations during stable or incrementally changing environments. However, when this change is discontinuous, there is a persistent need for continuous renewal of the basic premises underlying the 'best practices' stored in organizational knowledge bases. -- Yogesh Malhotra in Knowledge Management in Inquiring Organizations" - Vice President, SAP, North America in SAP Portals ASUG Meeting |
 |
| "Often used synonymously, the terms knowledge and information, are actually different. Information facilitates knowledge, and can exist without knowledge. Knowledge, however, cannot exist without information. To simplify the concept, Dr. Yogesh Malhotra, renowned scholar on Knowledge Management, defines "Knowledge" as potential for action that has an immediate link to performance. This definition suggests that a person's response or action, or contextual consideration for future action, based on information, is knowledge." - VeriSign Inc. |
 |
| "It is generally agreed that the greatest challenges to knowledge management initiatives are resistance to change in both an organization's information-sharing culture and the business processes that occur as a result. K.M. Malhotra defined the problem as follows: Culture is the most difficult component of KM to define, quantify, measure and influence. However, the success or failure of an effective KM program is almost solely dependant upon whether an organization's culture encourages or hinders sharing and transferring knowledge freely within the organization's structure. One thing is certain: an organization's cultural predisposition toward the free transfer of knowledge is largely reflective of the proactive stance demonstrated by the organization's leadership." - Northrop Grumman |
 |
| "Il Knowledge Management essenzialmente coinvolge processi organizzativi che cercano di realizzare una combinazione tra le capacità di elaborazione di dati e informazioni e le capacità creative e innovative degli esseri umani. (fonte: Yogesh Malhotra, Ph.D., Knowledge Management for the New World of Business...)" - Microsoft, Italy |
 |
| "Knowledge Management refers to the critical issues of organisational adaptation, survival and competence against discontinuous environmental change. Essentially it embodies organisational processes that seek synergistic combination of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings. This definition proposed by Dr. Yogesh Malhotra summarises a key issue for e-learning strategies and the way they will impact professional training and companies' organisation policies." - European Commission |
 |
| "In the Committee's view, definitions that treat the area as a discipline rather than a mere collection of technologies best encapsulate what knowledge management means. For example, Malhotra says:, "Knowledge Management caters to the critical issue of organisational adaptation, survival and competence in the face of increasingly discontinuous environmental change..." - Parliament of Victoria, Australia |
 |
| "It is therefore impossible to typify the roles of Knowledge Management workers other than the CKO, and indeed these roles themselves are in a constant state of change. Dr. Yogesh Malhotra defines this as follows: Given the need for autonomy in learning and decision making, such knowledge workers would also need to be comfortable with self-control and self-learning." - Government of UK |
 |
| "We are facing "permanent white-waters" which demands strategies for adaptation to uncertainty in contrast to the conventional emphasis on optimisation based on prediction (Malhotra 1999). To quote a decision-maker in a large multinational firm; "The future is moving so quickly that you can't anticipate it. We have put a tremendous emphasis on quick response instead of planning. We will continue to be surprised, but we won't be surprised that we are surprised. We will anticipate the surprise." (Malhotra 1999)." - Government of Sweden |
 |
| "It is difficult, not to say impossible, to replace the significance of individual or collective face-to-face interactions in the sharing of tacit knowledge and articulating it as explicit in an organization, even if rapid development of interactive multimedia applications combining text, image and sound offers increasingly advanced communication potential. Virtual forms of working and work organization might at best supplement, but never totally replace, self-managing teams with close physical and social contacts, for instance, as a forum for learning. (Malhotra) " - Government of Finland |
 |
| "A key feature of knowledge management is the sharing of knowledge as opposed to simply the dissemination of information. Knowledge has a different quality to information. Knowledge includes human experience and the ability to make complex judgments based on past experience. Information is more about mere data whereas knowledge is 'potential for action'. (Malhotra) - Government of Australia |
 |
| "Ich glaube die Technology ist der leichtere Teil des Ganzen. Die wirkliche Herausforderung stecken doch darin wie die Geschäfts-Prozessen und die darauf aufbauenden Geschäfts- Modelle in Einklang gehalten werden mit den radikalen änderungen in der Geschäftswelt und dem Berufsbild der "Knowledge Worker."[Malhotra, 1993]." - Government of Austria |
 |
| "Knowledge management refers to the critical issues of organizational adaptation, survival and competence against discontinuous environmental change. Essentially it embodies organizational processes that seek synergistic combination of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings," says Dr. Yogesh Malhotra, founding chairman and chief knowledge architect of the BRINT Institute, in an interview with Alistair Craven. Widely recognized as a knowledge management pioneer, Malhotra adds, "Knowledge management is more about the pragmatic and thoughtful application of any concept or definition, as it is not in the definition but in real world execution where opportunities and challenges lie. Any definition therefore must be understood within the specific context of expected performance outcomes and value propositions that answer the question 'Why' about relevance of KM."" - U.S. Embassy, American Center, New Delhi, India |
 |
| "Knowledge management, which is a new field emerging from the confluence of organisation theory, management strategy and management information systems, is viewed as an essential driver for innovation. According to Malhotra "Knowledge Management caters to the critical issues of organisational adaption, survival and competence in face of increasingly discontinuous change. Essentially it embodies organisational processes that seek a synergistic combination of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings"." - Government of South Africa |
 |
| "Estes ativos do conhecimento aumentam com o uso e daí a importância de as empresas identificarem o que sabem e manterem todo o esforço para desenvolverem área de gestão do conhecimento. A gestão do conhecimento, segundo Malhotra é a capacidade de catalizar os aspectos críticos de adaptação, sobrevivência e competência, buscando uma combinação sinérgica da capacidade de processar informações e conhecimento com a capacidade criativa e inovativa dos seres humanos. (MALHOTRA, 1999)." - Government of Brazil |
 |
| "Esta enumeración no implica que algún factor no pueda ocupar a la vez distintas posiciones. La principal característica del nuevo entorno de las organizaciones es su alto nivel de incertidumbre. Por incertidumbre entendemos "la diferencia entre la cantidad de información requerida para realizar una tarea y la cantidad de información ya en poder de la organización" YOGESH, Malhotra."" - Government of Argentina |
 |
| "The disconnect between IT expenditures and the firms' organizational performance could be attributed to an economic transition from an era of competitive advantage based on information to one based on knowledge creation." - Yogesh Malhotra - Government of Mauritius |
 |
| "The focus of knowledge management is on 'doing the right thing' instead of doing things right’, (Yogesh Malhotra, 2001). The emphasize is that that knowledge management provides framework within which the organization views all processes of the activities to sustain the business and/or ensuring the business survival. Within the army organization, there is no difference. The army needs to keep pace with the technology advancement preparing for the increasingly dynamic and unpredictable regional and world environment." - Royal Military Police Directorate, Army HQ, Malaysia |
 |
| "Knowledge Management embodies organnizational processes that seek synergistic combinations of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings." -- Yogesh Malhotra, Ph.D." - Government of Malta |
 |
| "Dr. Yogesh Malhotra, one of the experts and founder contributor in the development of concept of KM has defined the KM as under : "Knowledge Management caters to the critical issues of organizational adaptation, survival and competence in face of increasingly discontinuous environmental change. Essentially, it embodies organizational processes that seek synergistic combination of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings". As it is clear from this definition that objective of Knowledge Management as a crucial management function is not only to survive under changing environment but also to make the organisation adaptable and competitive. The same is particularly applicable for Banks in India, since they are now operating under such a dynamic business environment." - Indian Banks' Association, India |
 |
| "Dr. Yogesh Malhotra, the Founder and Chief Knowledge Architect of BRINT, and a well-known expert in the field of K-economy, opines: "The challenges facing us as we enter the 21st Century are formidable. Globalization, Information Technology and Shareholders' Values are transforming the world. To meet these challenges is to become a knowledge-creating or knowledge intensive organization"." - Indian Banks' Association, India |
 |
| "Knowledge Management has structural and functional basis in the IM (Information Management or IRM. The main difference is the high degree of dynamic activity involved in the KM system. To summarize in the words of Dr. Malhotra, (10) 'use of the information and control systems and compliance with pre-defined goals, objectives and best practices may not necessarily achieve long-term organizational competence. This is the world of 're-use,' 're-engineering', 're-cycling' etc, which challenges the assumptions underlying the 'accepted way of doing things.' This world needs the capability to understand the problems afresh given the changing environmental conditions. Knowledge management focuses on 'doing the right thing' instead of 'doing things right.'" - Indian Statistical Institute, Bangalore, India |
 |
| "Knowledge Management caters to the critical issues of organizational adaption, survival and competence in face of increasingly discontinuous environmental change. Essentially, it embodies organizational processes that seek synergistic combination of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings." - National Academy of Psychology (NAOP), India |
 |
| "Finally, all who are concerned with IT security issues should understand -- and appreciate -- the difference between information and knowledge. Information, writes Yogesh Malhotra, PhD, is embedded in a computer -- while knowledge is embedded in people. "Information generated by a computer is not a very rich carrier of human interpretation for potential action," he writes. "Computer are merely tools, however great their information-processing capabilities may be." - Chairman of the Board, The Institute of Internal Auditors |
 |
| "Leadership Quote of the Week: The focus of knowledge management is on doing the right thing instead of doing things right... Yogesh Malhotra" - Chartered Management Institute, UK |
 |
| "Dr. Yogesh Malhotra, founder of the Brint Institute and a pioneer in knowledge management, posits that "the basic premise is that you can predict how and what you'll need to do and that IS can simplify this and do it efficiently". However, the new business model, he says, is marked by fundamental, not incremental, change and businesses can't plan long-term. Instead, they must shift to a more flexible "anticipation of surprise" model, making it impossible to build a system that can predict what is the right information to be delivered to the right person at the right time. This is not to say that information technology has been displaced from the knowledge management equation; its place has been preserved by a growing realisation among developers that software alone cannot automatically be seen as the solution." - National President of the Australian Computer Society, Australia |
 |
| "Yogesh Malhotra, founding chairman and chief knowledge officer for the BRINT Institute in Syracuse, New York, believes that the fundamental distinction between data and knowledge plays a major role in whether a system is designed for adaptation and quick response to change. "Dynamic and radically changing environments overwhelm the deterministic logic of a structured model, resulting in a 70 percent failure rate that has characterized implementations of knowledge management models" says Malhotra. Recounting his visit to a Silicon Valley hi-tech consulting firm, Malhotra attributes most failed corporate intranet initiatives to the above fallacy... Malhotra says that once routinized for efficiency and optimization, knowledge-harvesting processes may be delegated to others. However, supply managers need to be more proactively involved in knowledge-creation and knowledge-renewal processes..." - Institute for Supply Management (ISM) |
 |
| "Yogesh Malhotra, founding Chairman and Chief Knowledge Architect of the BRINT Institute states: "Knowledge management software is not a canned solution; "Knowledge management technologies cannot always deliver the right information to the right person at the right time; "Information technologies cannot store human intelligence and experience; "Knowledge management systems do not account for renewal of existing knowledge and creation of new knowledge; "Greater incentives are needed for workers to contribute quality content to KMS." Improper use of KMS databases can waste resources if an organization does not really know what knowledge assets it possesses and fails to capitalize on potential new initiatives." - National Association of Realtors |
 |
| "Similarly, Dr. Yogesh Malhotra, the famous "Knowledge Architect", wrote a cautionary article on "When Best [Practices] Becomes Worst", Momentum: the Quality Magazine of
Australasia, Quality Society of Australasia, NSW (Australia, 2002). In fact, the conditions for producing and utilizing knowledge workers are not a question of the persons concerned merely acquiring subject-matter expertise, problem-solving competency
and communication skills. It is essential to provide an environment where such persons can
operate and flourish. In the same vein, one of Malhotra's recent books (monograph) for UNESCO discusses knowledge work taking place in "hyper turbulent organizational environments."" - International Labour Office (ILO) |
 |
| "Knowledge Management - Discipline that seeks to improve the performance of individual organizations by maintaining and leveraging present and future value of knowledge assets, encompassing both human and automated activities. " Knowledge Management caters to the critical issues of organizational adaption, survival and competence in face of increasingly discontinuous environmental change.... Essentially, it embodies organizational processes that seek synergistic combination of data and information processing capacity of information technologies, and the creative and innovative capacity of human beings." - Dr. Yogesh Malhotra" - U.S. Department of Health & Human Services |
 |
| "The mechanistic model of information processing and control based upon compliance is not only limited to the computational machinery, but extends to specification of goals, tasks, best practices and institutionalized procedures to achieve the pre-specified outcomes." -- Yogesh Malhotra - European Health Management Association, Ireland |
 |
| "KM has become an increasingly important management discipline in recent years. Nevertheless, some say the phrase KM is unhelpful because 'knowledge is not a "thing" that can be "managed"1. They challenge the 'dominance and control model' that often underlies traditional views of knowledge and organisational management and development. They assert instead the notion that knowledge is largely cognitive, tacit and highly personal. They champion the fundamental role of people and the social interactive basis of knowledge sharing and creation. (Malhotra, Y..) " - UK Department of Health |
 |
| "Knowledge management is viewed as an essentialdriver for innovation. According to Malhotra, "Knowledge Management caters to the critical issuesof organisational adaptation, survival and competencein the face of increasingly discontinuous change.Essentially it embodies organisational processes thatseek a synergistic combination of the data andinformation processing capacity of informationtechnologies, and the creative and innovative capacityof human beings"." - United Nations Development Program (UNDP), Geneva, Switzerland |
 |
| "Adaptive Learning (See: Double Loop Learning): "Adaptive learning, or, single-loop learning, focuses on solving problems in the present without examining the appropriateness of current learning behaviors." -- Malhotra, Y., Organizational learning and learning organizations: an overview." - World Health Organization (WHO) |
 |
| "Dr. Yogesh Malhotra is regarded among the world's most influential practitioners and thought leaders on knowledge management. Widely recognized as a knowledge management pioneer, in this extensive interview read what Dr. Malhotra has to say about knowledge, information, technology and chasing success in this field." - Emerald Group Publishing Ltd (UK) |
 |
| "Dr. Yogesh Malhotra in the US is a leader in the knowledge management field. In a recent article written for the US Journal for Quality & Participation, he has pointed to a problem in relation to organisations investing heavily in information technology but not realising gains in terms of knowledge creation." - Irish Times, Ireland |
 |
| "Be that as it may, there is no doubt that domestic enterprises, faced by a complete bankruptcy of knowledge and ideas, will, some day, understand the value of the knowledge held by their employees. In the meantime, they would do well to study the writings of Dr. Yogesh Malhotra, an authority on technology and innovation management, business performance, and corporate strategy issues related to information systems, knowledge management, e-business and electronic commerce, business decision models, and new organisation forms." - The Hindu, A Major National Daily Newspaper, India |
 |
| "Professor Yogesh Malhotra of Syracuse University, New York, and expert in this field, has recently argued that one of the reasons for this failure is that more often than not knowledge management is practiced in isolation and does not take into account the dynamism of the external environment." - Malaysian Business, Malaysia |
 |